We generally get confused between these two terms. These two technologies are the basis of the security mechanisms. In many host-based systems, both the mechanisms performed by the physical hardware and by the software in some cases.
There is a big difference between these two technologies.
Authentication: It is the mechanism to know that the identity is the same identity that he claims to be. The system securely identifies its users.
It generally answers two Questions:
Who is the user?
Is the User really the Person he claims to be?
This system simple password-dependent system or complicated as the Kerberos system. In any case, the Authentication system depends on some unique information that known to the individual only to be authenticated and the authentication system.
This information can be anything between passwords, Some physical properties like fingerprints, retinal patterns, etc, or some derived data. In this system, the System challenges the user to provide unique information. If the system verifies the data provided then the user considered authenticated.
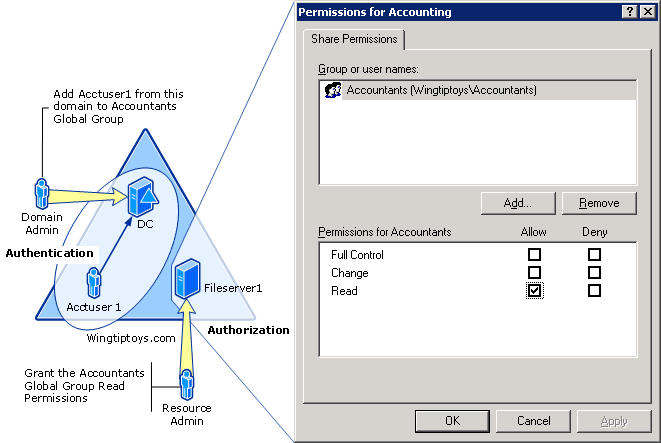
Authorization: This mechanism varies from the earlier mechanism.
Once the user-identified Authorization comes into the picture. In this mechanism, the system can identify what kind of user has logged onto the system i.e what level of access a particular authenticated user has.
For example, a simple Windows XP operating system can have many users logging onto a system with different user accounts such as Admin, guest, or some personalized logins. Every user account has different rights and authorities which are defined by the system.
Authorization is the mechanism that answers the following questions:
Is the User authorized to access Resource R
Is the User authorized to perform operation P
Is the User authorized to perform operation P on resource R.
These two mechanisms are tightly coupled mechanisms with each other.