A DDos attack is Denial of service attack or distributed denial of service attack, in which the computer resource is made unavailable to the users. This attack emerged as one of the most news worthy as the weaknesses of the internet. The means to carry out the attack can be different but the motive is same. There are several tools on computers that allow vandals to remotely control the resources to encounter an attack on the users computer to be inoperable. The nature of the attack is that it becomes impossible to stop in one attempt and single handedly. The basis of the attack is to flood the users computer with traffic.
DDos attack involves encountering into hundreds or thousand of machine all over the internet. After this the attacks installs DDos software on them which allows them to control these machines to launch the attack at ones on an organized way. These attacks exhaust bandwidth, router capacity , network resources etc.

There are two means of attacks Wireless and wired.
Some basic type of attacks include:
- consumption of the resources
- Disruption of routing information
- Disruption of state information.
- Disruption of network consumption
- Obstruction in media between the users and resources.
Why it is difficult to halt such attacks?
- The flood of the traffic makes the network shut down which makes it difficult to trouble shoot the problem
- Some times the victim may be able to filter the traffic by using the firewall, however this also nit effective it will degrade the performance If the attack is overloaded filter is useless.
- The traffic that comes from different compromised computers. To stop this traffic it requires to trace each address, then contacting that organization and ask them to stop the traffic.
- Many of the DDos attack tools allows to forge the there source address which makes even more difficult to trace the address.
- Once the source machines are identified the victim must ask to shut down the compromised computer. Now the source organization and staff may not be working on weekends or in nights, language barrier, the authority with the staff may not be sufficient and they may also be not familiar to the attack
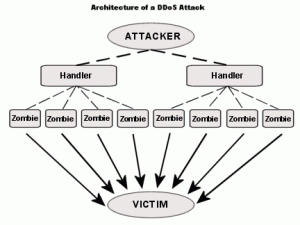
What measures we can take?
Linux/Unix computer :
Follow R.U.N.S.A.F.E Guidelines.
Download and run the test programs from the National protection Center to test these type of attacks
Windows :
Follow R.U.N.S.A.F.E Guidelines.
These precautions may help you to prevent the attacks